23-01-11-ECC
Some basics about elliptic curves. Make a description about ECC, and show the attacks and conversions to code.
ECC is somewhat difficult, and also the analysis which is necessary ought to be detailed.
The ECC always connects to the usage of sagemath, this post also introduces some common usages about ECC in sagemath.
PARALLEL
Assume: Parallel lines intersect at infinity which is called the infinity point P. (parallel and intersecting unity)
The properties of infinite P:
- The infinite
Pof Line L has only one. - The lines which are parallel to each other have the public infinite $P_{\infty}$.
- Any lines which are intersect have different infinite points $P_{\infty}$s. (If they have public infinity, it will contrary to assumption.)
- All infinity points formulate a infinity line.
- The total infinity points and all ordinary points in the plane form the projective plane.
PROJECTIVE PLANE COORDINATE SYSTEM
Formulate: Make $x = X/Z$, $y = Y/Z$, ($Z \neq 0$), and the Point A is $(X:Y:Z)$.
The infinity points are expressed as $(X:Y:0)$. The ordinary points is $Z \neq 0$,and the infinities are $Z = 0$, meaning that the equation of infinity points is $Z = 0$.
Thus, $(X:Y:Z)$ is called as projective plane coordinate system.
ELLIPTIC CURVE
Definition: The elliptic curve in projective plane satisfies the equation that $Y^2Z + a_1XYZ + a_3YZ^2 = X^3 + a_2X^2Z + a_4XZ^2 + a_6Z^3$, or Weierstrass homogeneous equation $Y^2=X^3+AX+B$, where the whole points are non-singular or smooth.
Non-singular/Smooth: Mathematically, the partial derivatives $F_x(x,y,z), F_y(x,y,z),F_z(x,y,z)$ at any point on the curve cannot be 0 at same time, meaning that any point exists tangent.
Assume that $x = X/Z, y= Y/Z$ and substitute into the equation above, we can obtain $y^2 + a_1xy + a_3y = x^3 + a_2x^2+a_4x+a_6$ and also the slope is $k = (3x^2+2a_2x+a_4 - a_1y)/(2y + a_1x+a_3)$.
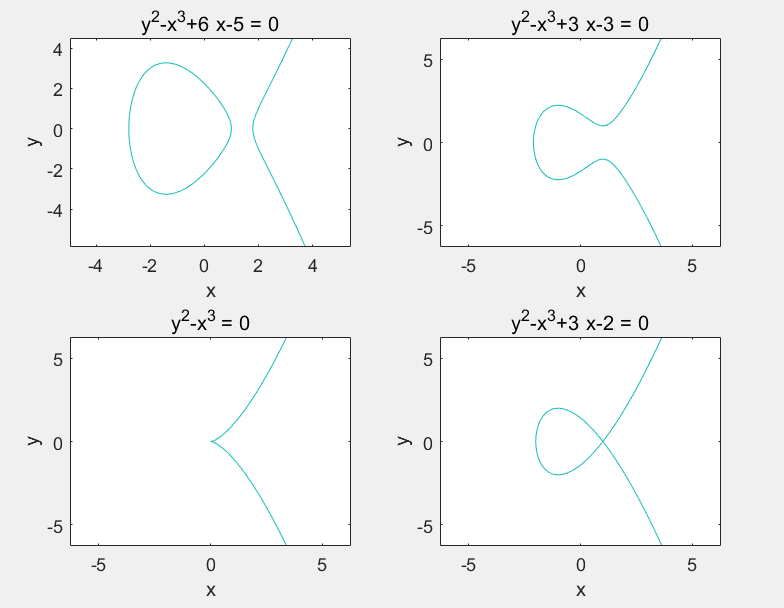
Two curves below which are not satisfied the definition are not elliptic curves , and they are called Singular Curves.
ALGORITHM ON AN ELLIPTIC CURVE
Algorithm: Arbitrarily take two points P and Q on the elliptic curve (if the two points P and Q coincide, then make the tangent of point P), make the line intersect the other point R' of the elliptic curve, and cross R' to make the parallel line of the y axis intersect the point R, we specify $P+Q = R$.
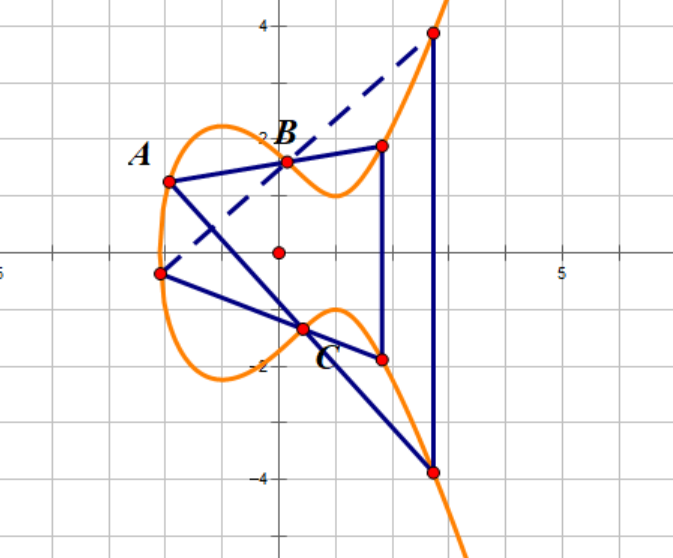
The infinity $O_{\infty}$ and the point $P$ on the elliptic curve intersect at the point $P$. The action of of infinity $O_{\infty}$ is equivalent to 0, which is called the zero element. The equation is that $O_{\infty} + P = P$.
Deduction:
- Three points on elliptic curve are in the straight line $A + B + C = O_{\infty}$.
- The sum of $k$ identical points is denoted $kP$. eg: $P+P+P = 2P+P = 3P$
Notice: Elliptic curves are not necessarily symmetric with respect to x-axis.
ELLIPTIC CURVE IN CRYPTOGRAPHY
Discretization: Define elliptic curves on finite field.
Algorithm:
Finite field $F_p$ only has finite elements.
$F_p$ has $p$ elements. $F_p \in {0, 1, 2, 3, \dots, p-1}$
+:$a + b \equiv c \mod p$
×:$a \times b \equiv c \mod p$
÷:$a \times b^{-1} \equiv c \mod p$
Unit element = 1 ; Zero element = 0
The elliptic curves that are suitable for encryption: $y^2 = x^3 + ax + b$.
The relationship among $P(x_1, y_1), Q(x_2, y_2)$ and $R(x_3, y_3)$:
- $x_3 \equiv k - x_1 - x_2 (\mod p)$
- $y_3 \equiv k(x_1 - x_3) - y1(\mod p)$
- $k$
- if $P = Q$, the $k = (3x^2 + a)/2y_1$
- if $P \neq Q$, the $k = (y_2 - y_1)/(x_2 - x_1)$
Point P exists the minimum positive integer $n$, which make $np = O_{\infty}$, and we will call $n$ as the order of n. Otherwise, it is called infinite order.
n always exists.
SIMPLE ENCRYPTION AND DECRYPTION ON ELLIPTIC CURVES
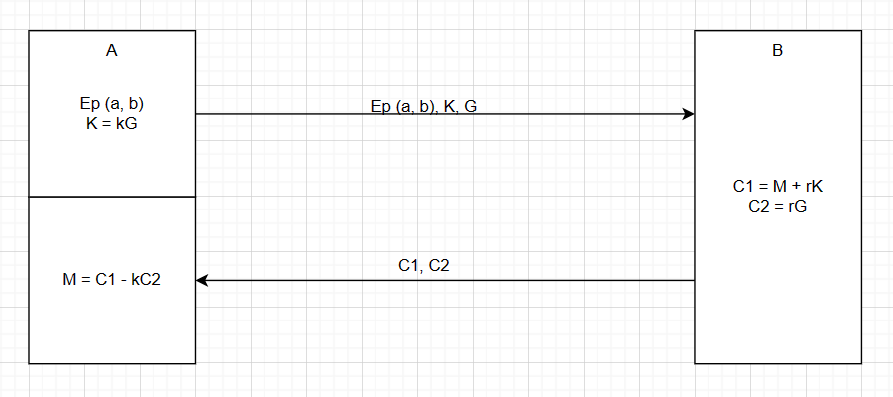
A as the generator and decryptor. B as the encryptor.
A generates the basic parameters. The $(a, b)$ is to generate the elliptic curve. The $G$ is the chosen base point. Then, send $E_p(a, b), K, G$ to B.
B generates the random $r$. Make a encryption and send $C_1 = M + rK,C_2 = rG$ to A.
A decrypts the ciphers by the equation $M = C1 - kG_2$. Finally, A will get message $M$.
PubKey: $K = kG$
PriKey: $k$
Common 6 parameters $F(p,a,b,G,n,h)$:
- $p, a, b \rightarrow E_p(a, b)$: $p$ 200 more digits can ensure the security.
- $G$: the chosen base point of $E_p(a, b)$
- $n$: the order of $E_p(a, b)$
- $h$: the cofactor and the integer part that $m$, the sum of all points on elliptic curve, divides $n$.
ATTACKs
The important part.
Make some description about the common attacks on elliptic curves in cryptography.
Pohlig-Hellman
The order of elliptic curve is factorized into small primes.
Main idea:
- Factorize the order.
- Discrete logarithmic problems in factorized primes.
- Chinese reminder theorem.
Deduction:

Example: ECC-2
1 | # polig_hellman |
Smart Attack
$E(F_p) = p$, the order of the elliptic curve is a prime.
It will be updated, if I have time.
Exp: ECC-3
1 | # smart_attack |
BSGS
baby step giant step
discrete_log(P,Q,operation = ‘+’)
Problems: $y^x \equiv z \mod p$
To solve out the $x$.
Original
$gcd(y, p) = 1$
Assume $x = am - b,m = \sqrt{p}$, $a \in [0, m), b\in[0, m)$.
Derivation:
$$
y^{am-b}\equiv z (\mod p)
$$
$$
y^{am} \equiv z \cdot y^{b}(\mod p)
$$
Brute force enumeration, enumerate the right in $[0, m)$ and calculate into list. At the same time, we enumerate the left in $[0, m)$, comparing the two list to find the $x$.
Extended
$gcd(y, p) \neq 1$
Assume $d = gcd(y, p)$.
Derivation:
$$
y^{x} + kp =z
$$
$$
y\cdot y^{x-1} +kp = z
$$
If we divide it by $d$., we will get that:
$$
\frac{y}{d}\cdot y^{x-1} + k \cdot \frac{p}{d} =\frac{z}{d}
$$
Recursive the equation, unless $d = 1 $. Assume that the product of all $d$ and we enumerate $c$ times. Thus, we can obtain the condition that $x’ = x -c, p’ = \frac{p}{g}, z’ = \frac{z}{g}$.
$$
y^{x’} \cdot \frac{y^{c}}{g} \equiv z’ (\mod p’)
$$
And it convert to the original BSGS.
Example: ECC-1
1 | # bsgs |
ECC
Definition
The equation:
$$
(a, b)\in F, y^2 = x^3 + ax + b
$$
$$
\Delta = 4a^{3} + 27b^{2} \ne 0
$$
if the ECC satisfies the equation, we calculate its discriminant by:
$$
y^2 + axy + by = x^3 + cx^2 + dx + c
$$
Test
1 | a = -5; b = 4 |
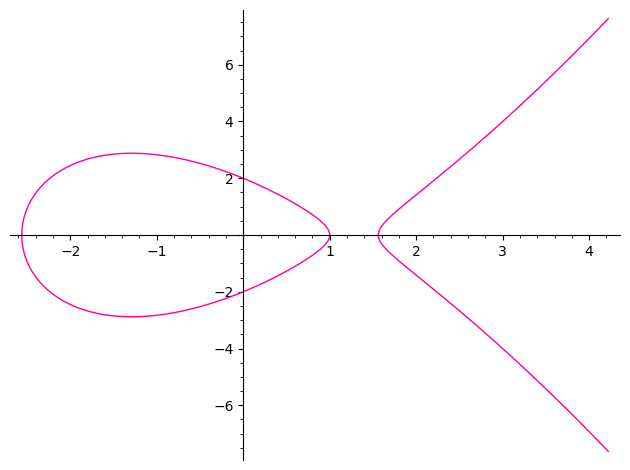
if we change the figure of $a$ and $b$, we can get the other EllipticCurves.
1 | a = 2; b = 3 |
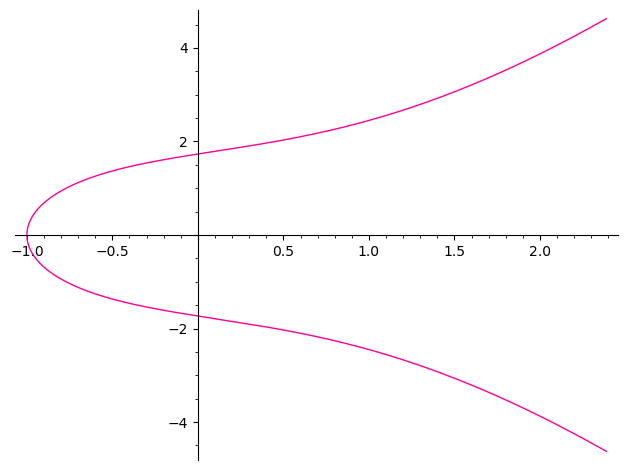
or we make the $a$ and $b$ random, thus we can not predict the curves.
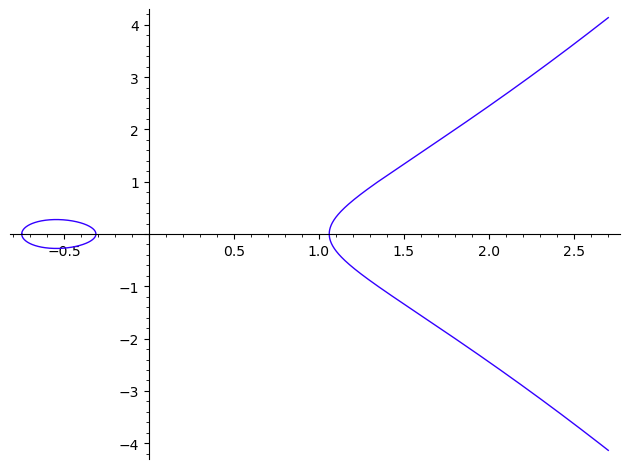
1 | E3 = EllipticCurve(RR, [RR.random_element(), RR.random_element()]) |
1 | sage: p = 137 |