22-12-21-UNknown
Figure out 2 tasks.
One is for crypto, and the other is for misc.
Both of them are easy.
poem
reference: [ACTF新生赛2020]base64隐写
- base64stego
- caeser cipher
base64stego
Make sure that the end of each line. This ending is \r\n
1 | import base64 |
caeser cipher
Just crack!
key is 13.
Alex2Bob
- ARCHPR-mask
- PNG-header
- PNG-crack width
- LSB
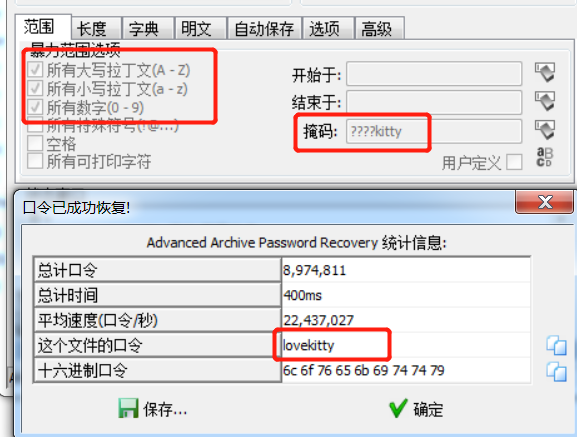
ARCHPR-mask
Known the end of the key is kitty.
This is the mask attack. We don’t know the length of the key, so we try some possibilities.
Until we try to set unknown length is 4, we get the key.
PNG-header
Use the winhex and analyze the png. We find that the file header is wrong, so we should edit the file header 88 -> 89.
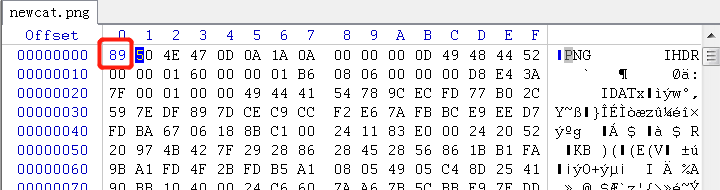
Still can’t open the picture or see the content.
PNG-crack width
Crack the true width, and we will get the width is 0x260.
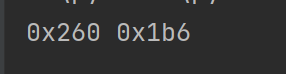
Edit the width by winhex or 010Editor, and we will get the real picture.

LSB
Two ways to get the information embedded in LSB.
- stegsolve-original
- zsteg
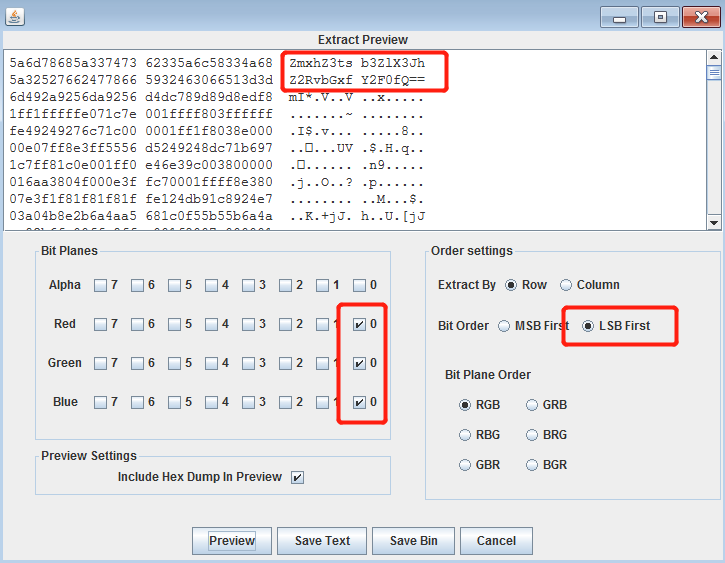
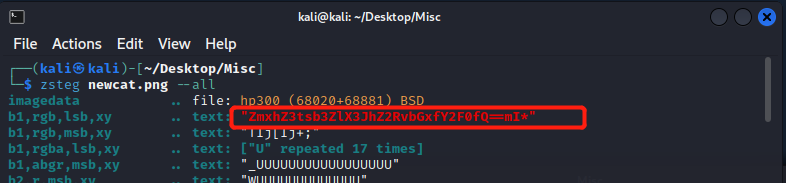
The cipher is ZmxhZ3tsb3ZlX3JhZ2RvbGxfY2F0fQ==, and base64 decode.