22-12-20-Encrypto-Wireshark
Some traffic packets may be encrypted. When I import the private key in one case, I can’t get the decrypted packets like http.
FinalIy, I search for this problem and get the solution.
This post aims to make a conclusion about the encrypted-traffic-packets(tls/ssl).
REFERENCE
Really thank for the article!
The second is to edit the configuration of computer, which can be caught in the direct way by using webshell.
DECRYPT TLS/SSL
There are three methods to decrypt the encrypted-ssl/tls packets.
- Use the
server's certor theprivate-keyto decrypt. - Use the
ssl-key-log-fileto decrypt. - Disable the config setting to decrypt packets which use the
Diffie-Hellman-Exchange.
Server’s cert/Private-key
preparation
- TLS/SSL packets
- cert or private-key
- wireshark
notice
The TLS/SSL packets should not relate to the Diffie-Hellman-Exchange and just a common encrypted packets.
CERT/PRIVATEKEY
The cert or private-key should not be encrypted. And usually, the private-key is the standard of PKCS#8.
If you have a binary DER, it cannot be used in wireshark, and we ought to make a convert.
1 | openssl pkcs8 -nocrypt -in der.key -informat DER -out pem.key -outformat PEM |
- der.key: the name and root of DER
- pem.key: the output file
And, the private-key ought to be like this:
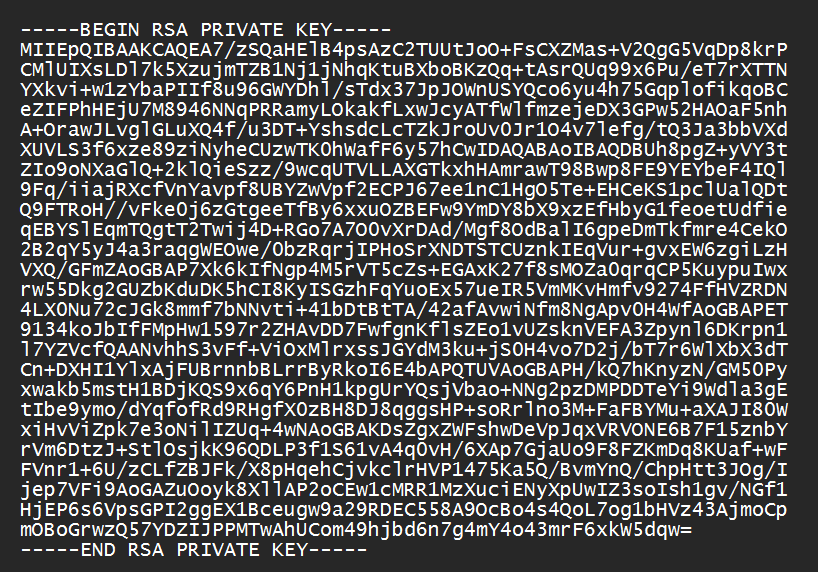
which shows that the beginning is -----BEGIN RSA PRIVATE KEY-----.
DECRYPT KEY
If the beginning is -----BEGIN ENCRYPTED PRIVATE KEY-----, we should decrypt the key in a proper way.
a common command is:
1 | openssl rsa -in [source file] -out [outfile] |
step
- OPEN the wireshark and import the private-key or cert.
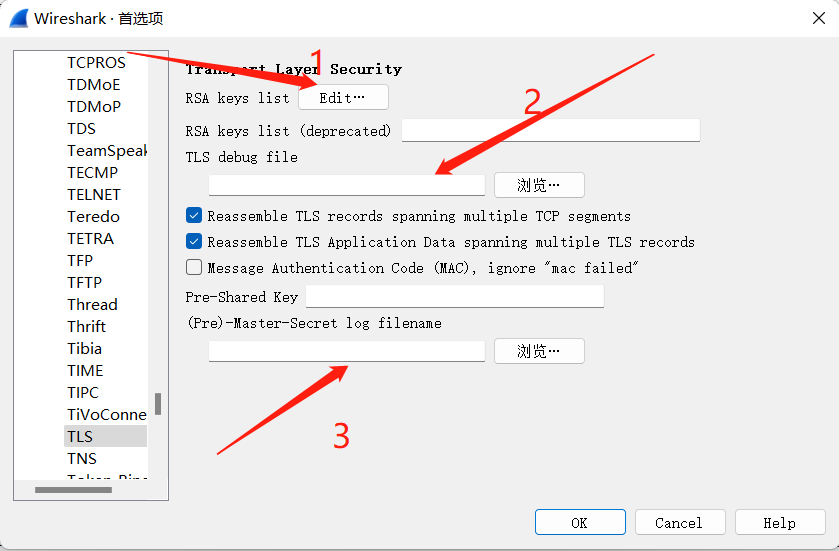
- RSA keys list. Import private key, add the
port,ip,protocol,rootand the chosenpassword. Mainly used. - TLS debug file. Some debug file.
- Master-Secret log. Key log file.
- If all things right, and we will see the
http traffic.
Key log file
Use the key log file. Usually, this file is in the traffic packets. The key log file is like this.
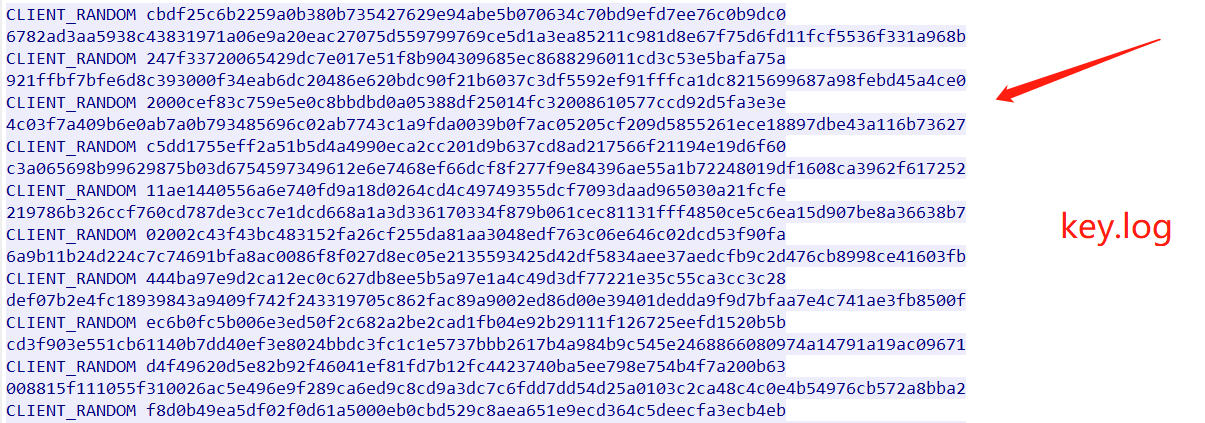
Relate to D-H
Sometimes, the encrypted traffic packets cannot be decrypted by using methods above.
how to recognize
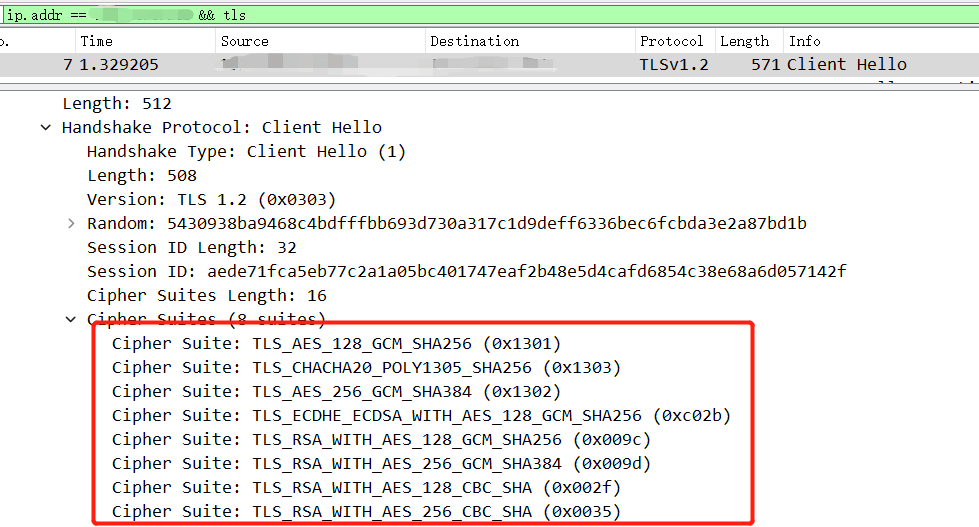
When we analyze the traffic packets, we use command like ip.addr == xxx.xxx.xxx.xxx && tls to find the target packets.
If we see the Client Hello, we should make a notice that it maybe a D-H encrypted traffic packet.
For example:
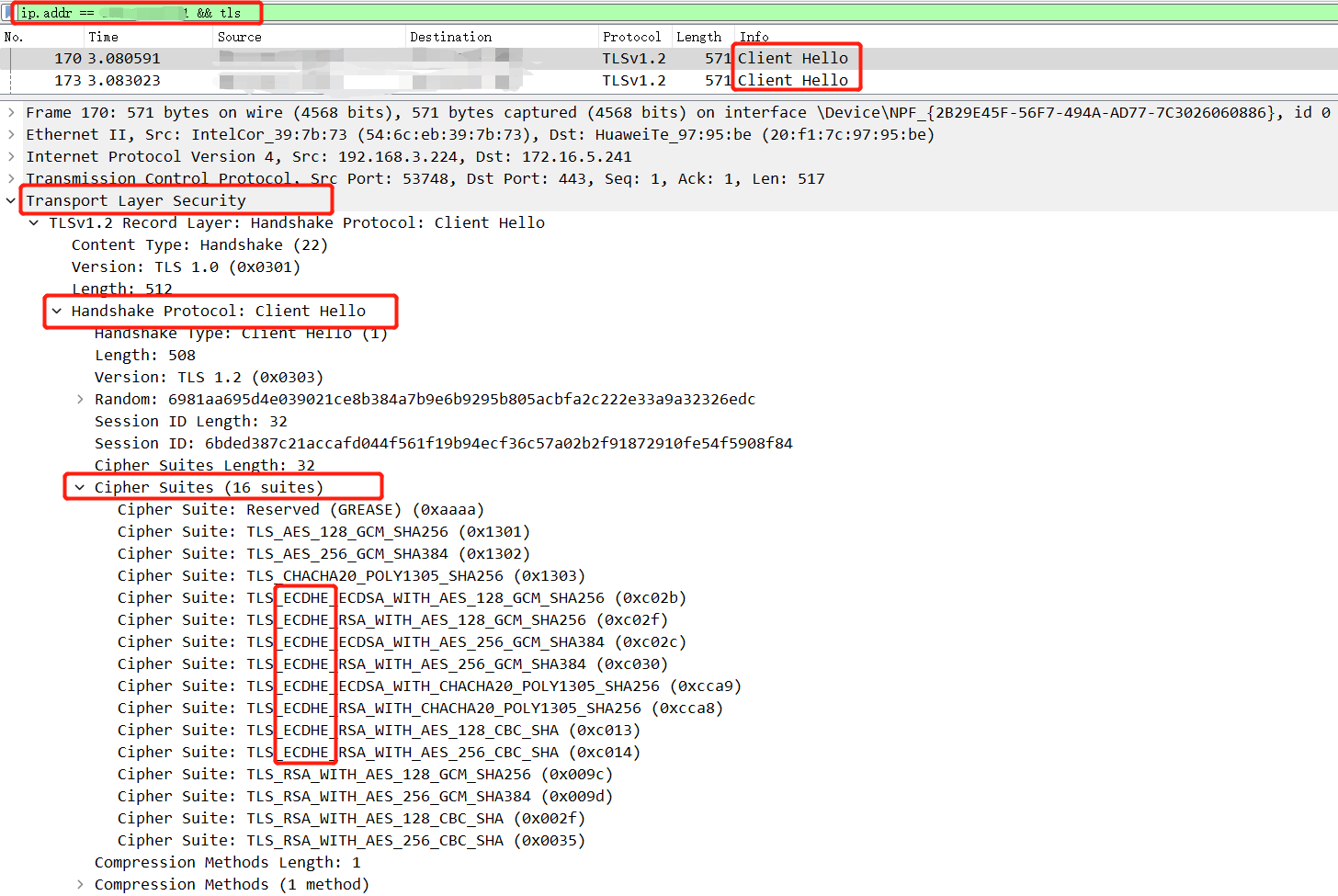
We can change the browser to catch the traffic again.
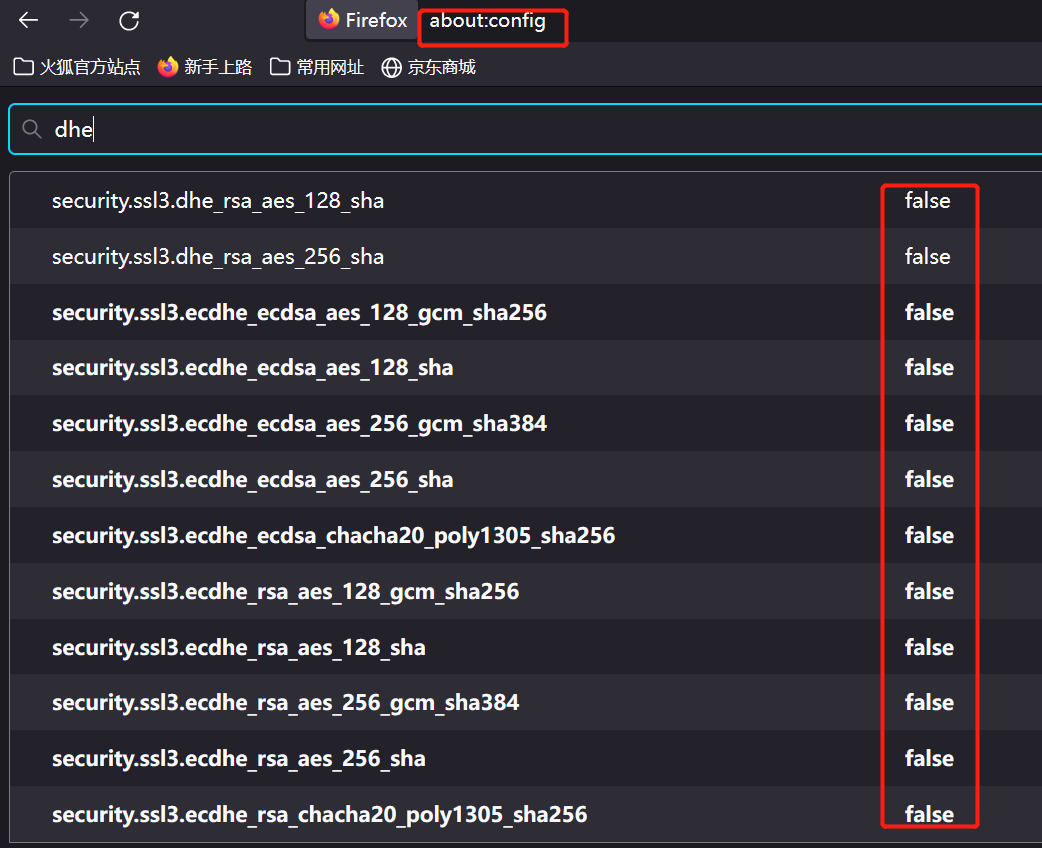
set the firefox
The address is about:config, and search for the dhe.
We can change the target according to the traffic packets or make all things false.
recatch the traffic and analyze
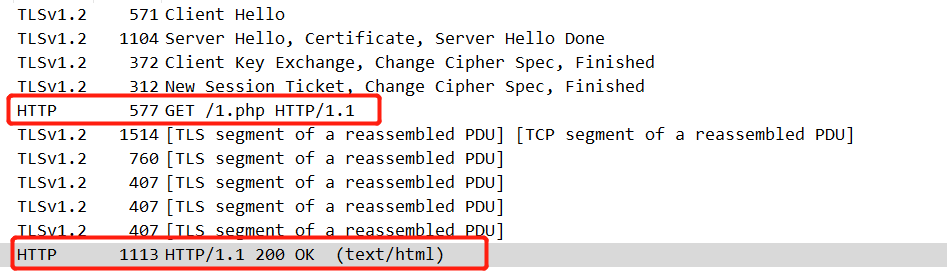
After importing the private key, we can see the decryptedhttp traffic.
CONCLUSION
The Diffie-Hellman-Exchange is really beyond my imagination.